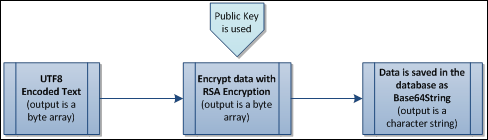
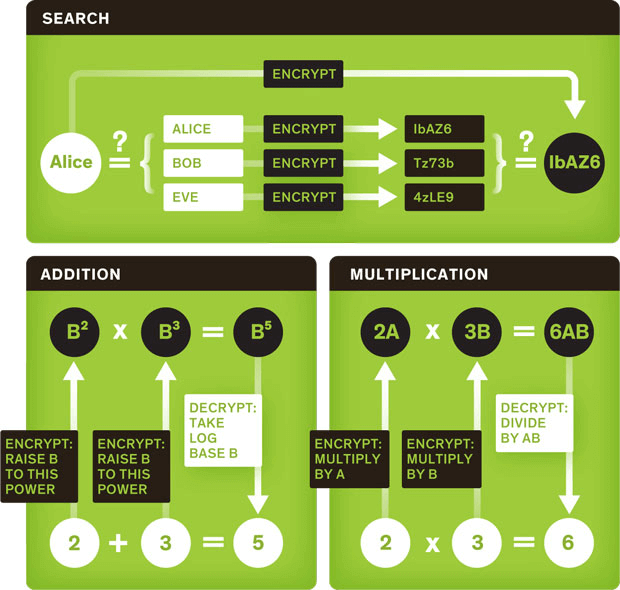
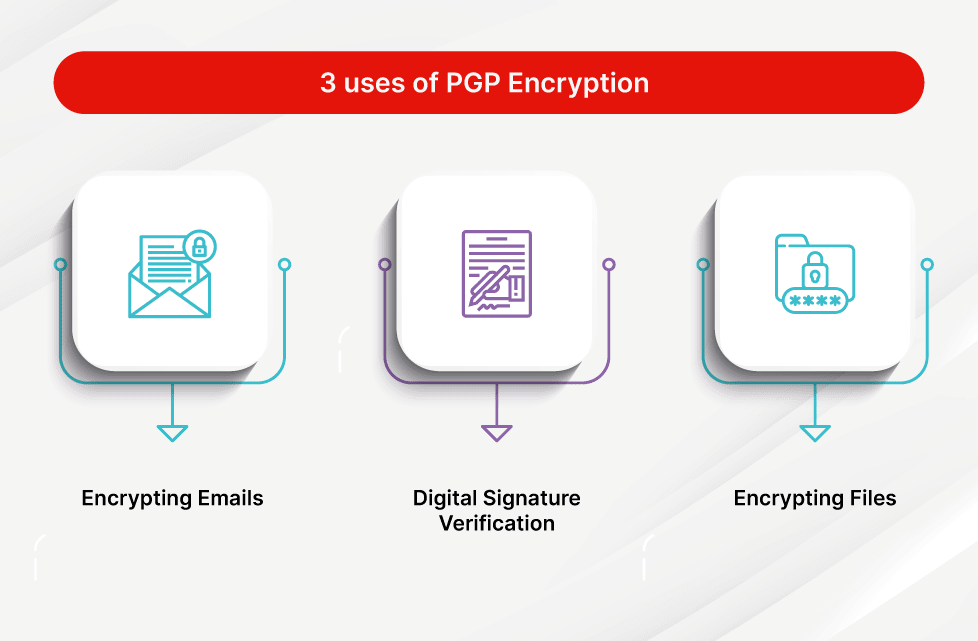
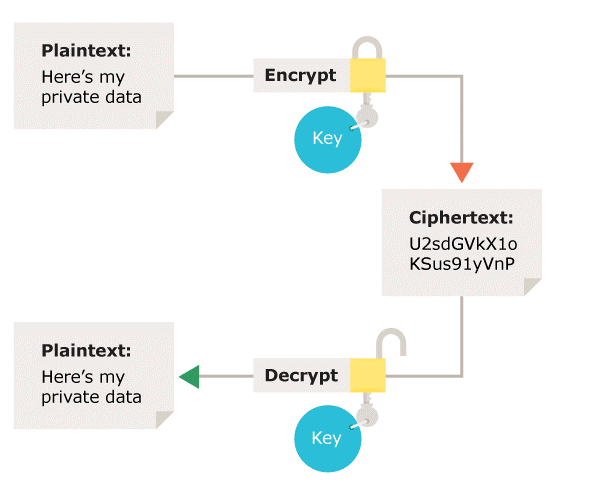
GitHub - magiclen/js-short-crypt: ShortCrypt is a very simple encryption library, which aims to encrypt any data into something random at first glance.
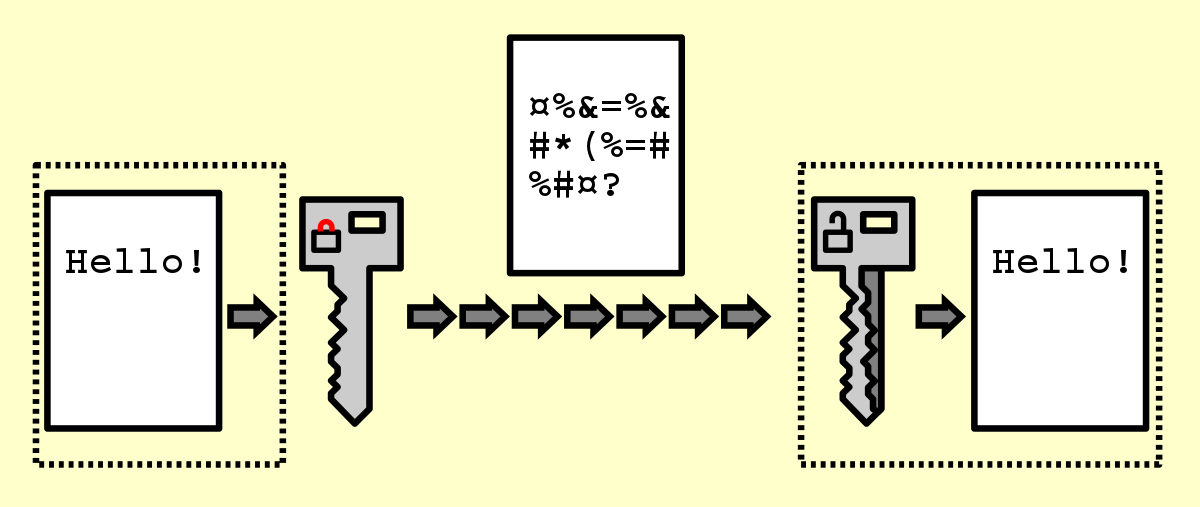
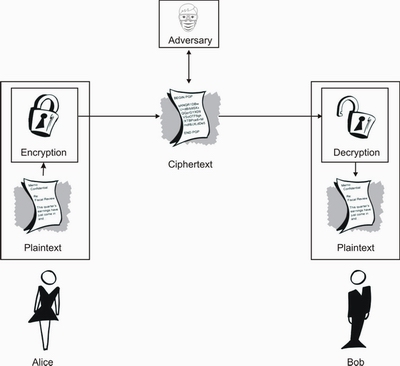
write an informal short essay discussing the difference between encryption and hashing Archives - Network Kings